Teams | Collaboration | Customer Service | Project Management
Vulnerability
Chrome Zero Day: Find vulnerable devices for patching
Chrome zero-day: find devices with vulnerabilities across your inventory
Zulip Cloud security vulnerability with reusable invitation links
An internal investigation recently uncovered a vulnerability (identified as CVE-2022-21706) in Zulip’s invitation links. Specifically, a reusable invitation link could be used to join a different organization than the one it was created for. As a result, there was a potential for users to join any organization without an invitation (and bypassing domain restrictions). This vulnerability was discovered by the Zulip security team, and has now been fixed for all Zulip Cloud organizations.
Log4j: Two Tricks to Make Your Next Vulnerability Less Chaotic
Tl;dr: Log4j is a mess, if you’re chasing down the applications, services and servers that use Java; consider the suggestions below to make zero day patching easier.
Coordinated disclosure of XML round-trip vulnerabilities in Go's standard library
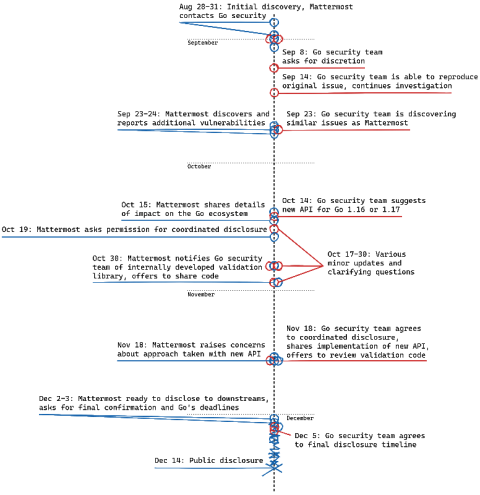
This blog post is a part of Mattermost’s public disclosure of three serious vulnerabilities in Go’s encoding/xml related to tokenization round-trips. The public disclosure comes as a result of several months of work, including collaborating with the Go security team since August 2020 and with affected downstream project maintainers since earlier this month.