Security
Elevating Trust and Security in B2B SaaS with Vivantio's SOC 2 Compliance
In an era where data security is paramount, Vivantio, a leading B2B SaaS Service Management Platform, proudly announces the successful completion of its SOC 2® assessment. This achievement underlines our unwavering commitment to providing secure and reliable service management solutions to our customers.
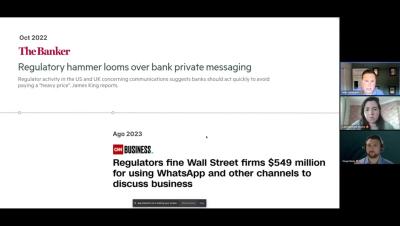
FINED! How Financial Services Can Avoid Paying Millions for Using Unsecured Messaging Apps
Network Overhead, Latency with Secure Access Service Edge (SASE)
Digital Experience Monitoring (DEM) has become an area of focus for Secure Access Service Edge (SASE) vendors. As businesses adopt SASE or security-as-a-service technology for compliance and security, they must consider the overall employee digital experience. SASE architectures add network overhead and impact performance, response times, and latency. In this article, we will delve into.
Software supply chain security: 12 strategies to reduce supply chain risks
Malicious code insertion, dependency poisoning, data exfiltration — these are worrisome words to organizations who deliver software products to customers. The complex process of deploying and maintaining software is fraught with supply chain risks, and the likelihood of an attack is higher than ever.
Secure your collaboration with Slack | Slack for Security
NSFW: Clicking for Thrills Could Lead to Systemic Ills
Explore the consequences of workplace adult content consumption on productivity and cybersecurity. Learn how Insightful’s business activity monitor can empower employers to monitor, educate, and safeguard their teams. Take action to secure your company's digital space now.
How to Safeguard Your Hybrid Workplace from Cyber Threats
With the rise of hybrid work, businesses face unique cybersecurity challenges. Discover how to prevent potential vulnerabilities and safeguard your hybrid workplace from cyber threats by implementing robust security solutions and using remote employee monitoring software.
5 most secure video conferencing apps for privacy-conscious organizations
Secure video conferencing is a crucial tool for organizations striving to communicate effectively without the fear of data breaches and malicious cybercrime attempts. The recent shift towards remote work has underscored the critical need for secure digital meetings. However, this reliance unveils several privacy challenges: According to research, 97% of IT professionals are concerned about video conferencing privacy and data protection, with 92% aware of existing security vulnerabilities.